Secure Azure DevOps Pipelines with Workload Identity Federation (OIDC) and Terraform
Date published:
Managing secrets and credentials securely in cloud has always been a challenge. Azure DevOps addresses this with Workload Identity Federation—a game-changing approach to authentication that eliminates the need for long-lived secrets. In this post, we’ll explore how it works, why it matters, and how to set it up in your Azure DevOps pipelines using Terraform.
What is Workload Identity Federation?
Traditionally, Azure service connections used service principals secured with secrets or certificates. While effective, this approach required frequent rotations and posed security risks if compromised.
Workload Identity Federation changes the game by leveraging OpenID Connect (OIDC). Instead of static credentials, it uses dynamically generated tokens for authentication. These tokens are short-lived, minimizing security exposure.
Why Does It Matter?
- No Secrets: Secrets are a common attack vector, and therefore, minimizing the need to store them is crucial.
- Simplified Management: No more manual secret rotations.
- Enhanced Security: Short-lived tokens reduce the risk of credential theft.
Setting Up Workload Identity Federation in Azure DevOps
-
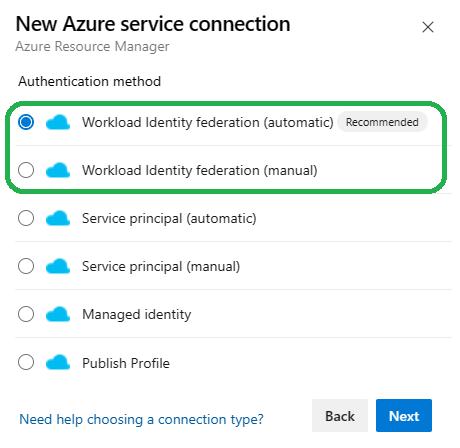
Create a New Service Connection
- Go to your Azure DevOps project.
- Navigate to Project settings > Service connections.
- Click New service connection and select Azure Resource Manager.
- Choose Workload identity federation (automatic) as the authentication method.
- Follow the prompts to configure the connection.
- Azure DevOps will automatically create federated credentials in Azure AD.
Pro Tip: Use descriptive names for your service connections to keep things organized.
Terraform Configuration Example
You can automate the setup process with Terraform. The example below creates the workload identity federation service connection in Azure DevOps using Terraform by using the Azure DevOps Terraform provider.
Convert Existing Connections
Already using a service principal? No worries—you can migrate to Workload Identity Federation (OIDC).
- Open Project settings > Service connections.
- Select the service connection to update.
- Click Convert and follow the prompts like the screenshot below.
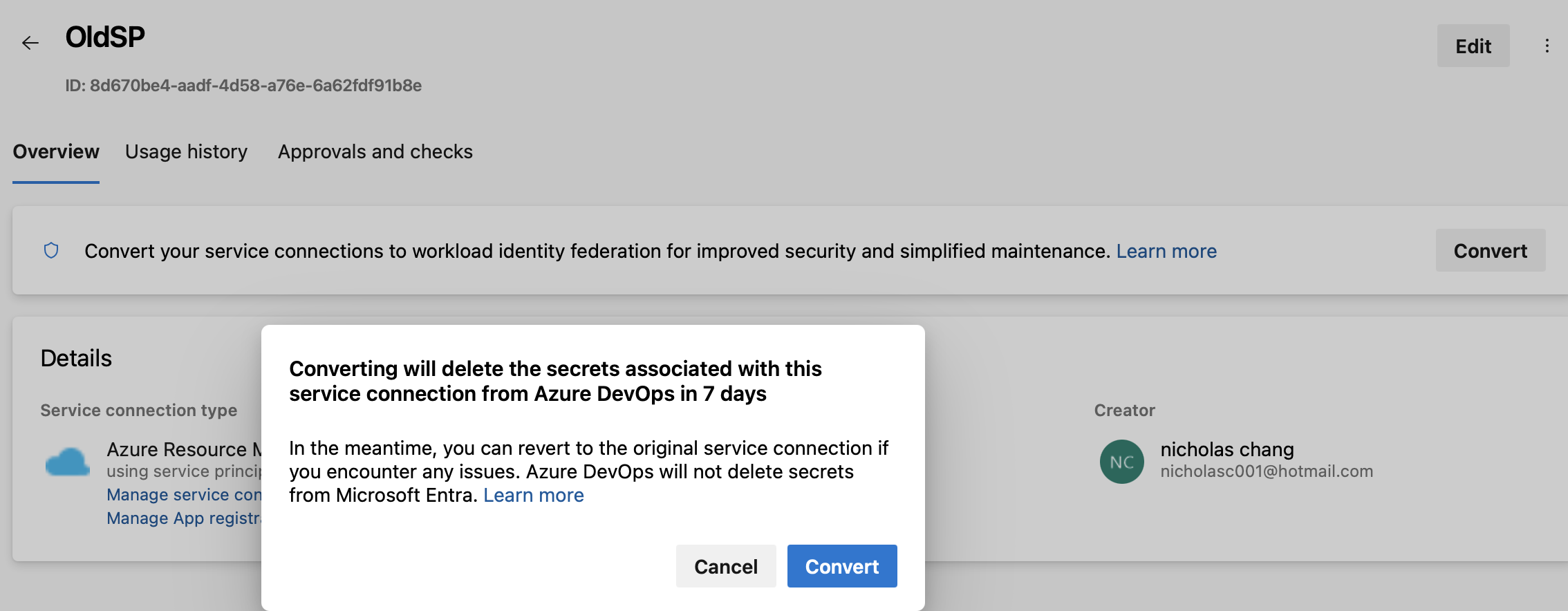
Once converted, the service connection will use OIDC for authentication instead of a service principal. You also have the option to revert to the original service principal if needed within seven days.
Adding Service Connection OIDC Permission to Azure DevOps
To use the OIDC service connection in your pipeline, you need to grant the necessary permissions. The service connection you created for OIDC must be added to the endpoint creator and reader role in Azure DevOps.
- Go to Project settings > Service connections.
- Select reader and endpoint creator role and add the service connection to it.
Setting up Pipeline
The important part of the pipeline is to add the ARM_USE_AZUREAD OIDC environment variable. This variable tells the Azure DevOps pipeline to use the OIDC service connection for authentication.
Conclusion
Workload Identity Federation offers a modern, secure, and efficient approach to managing credentials in Azure DevOps pipelines. By eliminating long-lived secrets, it reduces risk and simplifies operations.
References

