Microsoft DevOps Security in Defender for Cloud for Azure DevOps
Date published:
Overview

This post is my contribution towards Azure Spring Clean 2023 event organised by Azure Community Thomas Thornton and Joe Carlyle. This event is about community contributors share learning resources that highlight best practices and tips for Azure, which you can see at https://www.azurespringclean.com/
Last year, Microsoft introduced a new service in Defender for Cloud called Microsoft DevOps Security. This service is a part of the Azure Defender for Cloud suite, designed to help secure DevOps pipelines and detect suspicious activity.
In this blog post, I will show you how to set up Microsoft DevOps Security in Defender for Cloud and how to use it to monitor your Azure DevOps pipelines.
Azure DevOps used Microsoft Security DevOps Marketplace Extension. I will install another extension called SARIF SAST Scans Tab to view the results of MSDO analyser scans on the Azure DevOps pipeline runs. It will look at the SARIF files in the CodeAnalysisLogs artifact directory and display the results in the Scans tab.
Microsoft Security DevOps?
Microsoft Security DevOps (MSDO) is a command-line application that integrates static analysis tools for security and compliance into the development cycle. It is data-driven with portable configurations that enable deterministic execution across multiple environments. By using Microsoft Security DevOps, it can install, configures and runs the latest versions of static analysis tools. The MSDO can output the results in the pipeline runs under a Scans tab using the SARIF SAST Scans Tab extension on Azure DevOps.
The MSDO is a central system that, as part of Microsoft Defender for Cloud, provides your security teams DevOps insights across multi-pipeline environments, such as GitHub and Azure DevOps.
Some of the most common MDSO tools are:
-
Trivy - Vulnerability scanner for containers, suitable for CI
-
Terrascan - Open-source static code analyser for infrastructure as code to write secure IaC code
-
Credscan - Detects credentials in source code
-
Template Analyzer - Checks Azure Resource Manager templates for security and best practices
Integration with AzureDevOps?
To start with Microsoft Security DevOps, we must connect Azure DevOps to Defender for Cloud. You can do this by following the steps below:
- Log in to the Azure portal and navigate to the Microsoft Defender for Cloud service, and under Manage, select environments settings. Click on add environment and select Azure DevOps.
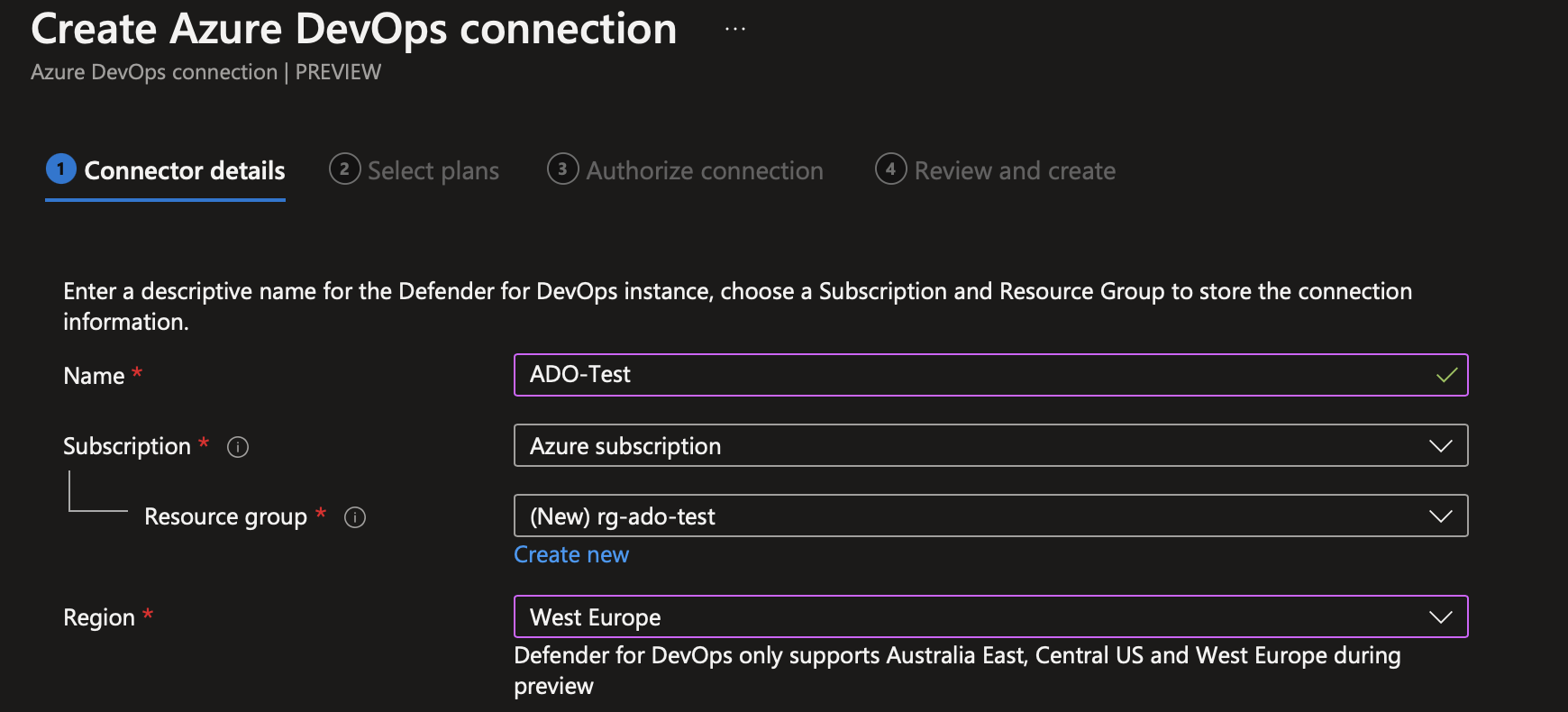
- Create an Azure DevOps connection by giving it a resource group, name and location. Currently, the only region it supports is West Europe, Australia East, and Central US. I created it in West Europe. However, I recommend deploying the resource in the same region as your Azure DevOps organisation or one close to it.
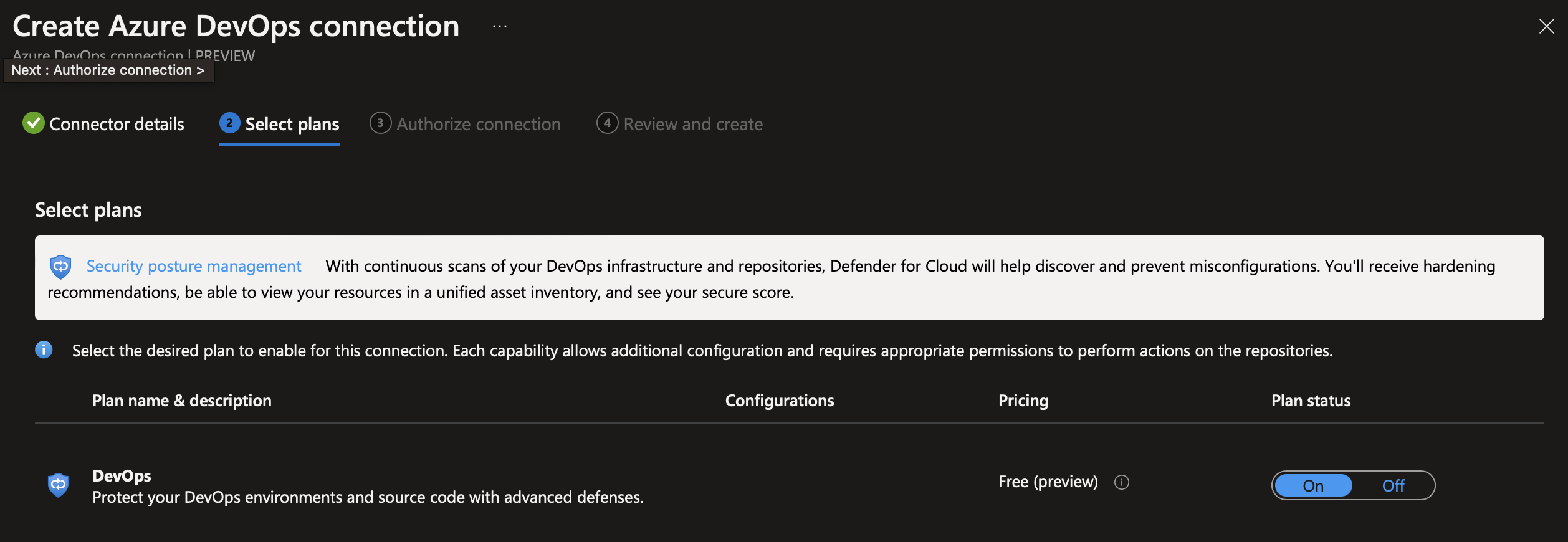
- Next, you will see the details of the plan. I have left it as the default plan status “on”. As you can see in the image below, the pricing is free and is currently under preview.
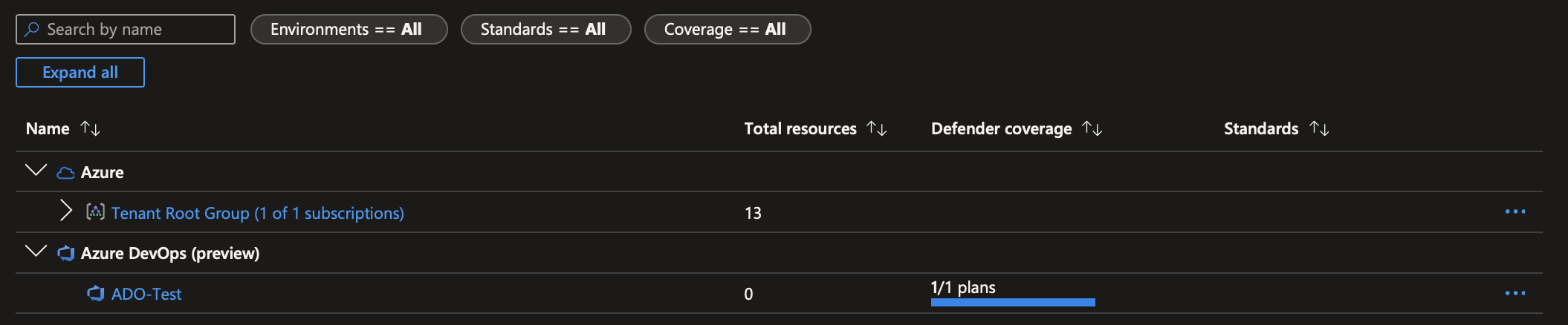
- This will direct you to the page where you need to authorise the connection. Click on Authorize to redirect to the Azure DevOps page for authorisation. Once the link to Azure DevOps is confirmed, you will be redirected back to the Microsoft Defender for Cloud page, like the image below.

Please select the correct Azure DevOps organisation and the project you want to connect to Defender for Cloud. I chose the auto-discover option in the organisation.
Click next to create the connection, and after several minutes, you will see the ADO connection on the environment settings page.
Set up Azure DevOps Extension?
Now that we have connected Azure DevOps to Defender for Cloud, we can install the Microsoft Security DevOps extension on Azure DevOps.
- Go to the Azure DevOps marketplace and search for Microsoft Security DevOps and SARIF SAST Scans Tab in the marketplace. https://marketplace.visualstudio.com
Install both extensions.
- Return to the Azure DevOps project and click on the Pipelines tab. Click the New pipeline button, select the repository you want to use, and choose the new starter pipeline. Please copy the code below and paste it into the YAML editor. You can find the sample code here: https://learn.microsoft.com/en-us/azure/defender-for-cloud/azure-devops-extension, or you can run any pipeline and add the Microsoft Security DevOps task to it.
|
|
- Click on the Save and run button to run the pipeline. Once completed, you will see the Microsoft Security DevOps task running and the results in the Scans tab.
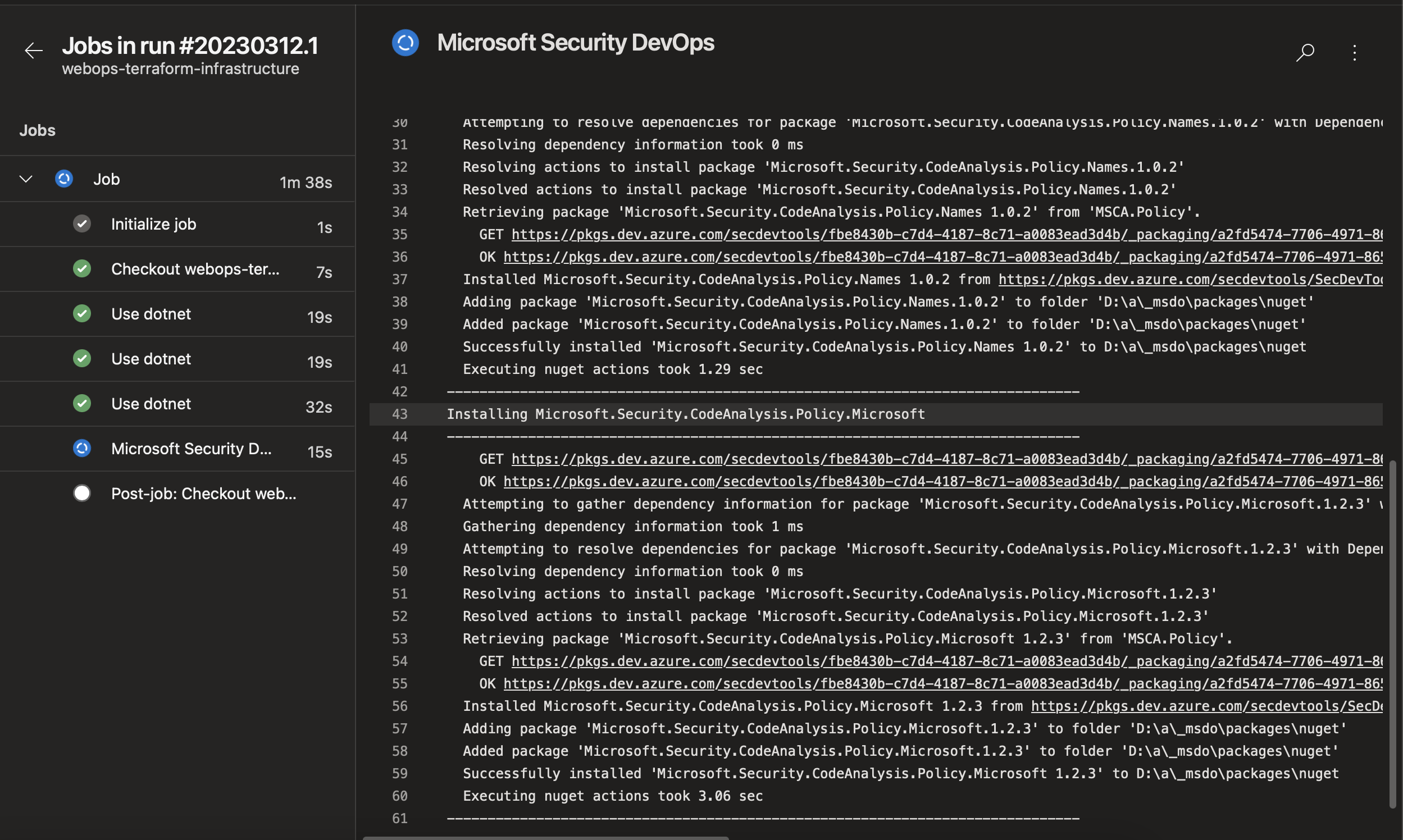
Security Vulnerability detected
The scan tab will report any security issues in the pipeline detected in your repository.

Enable Pull Request Annotations?
According to Microsoft, Defender for DevOps allows you to expose the above security findings as annotations in pull requests. Developers know the issue needs resolving before the code merges into the main branch.
- Go to Azure DevOps and go to your repo. Click on project settings and select the Repositories tab. Select your repository, navigate to policies, and select the main branch.
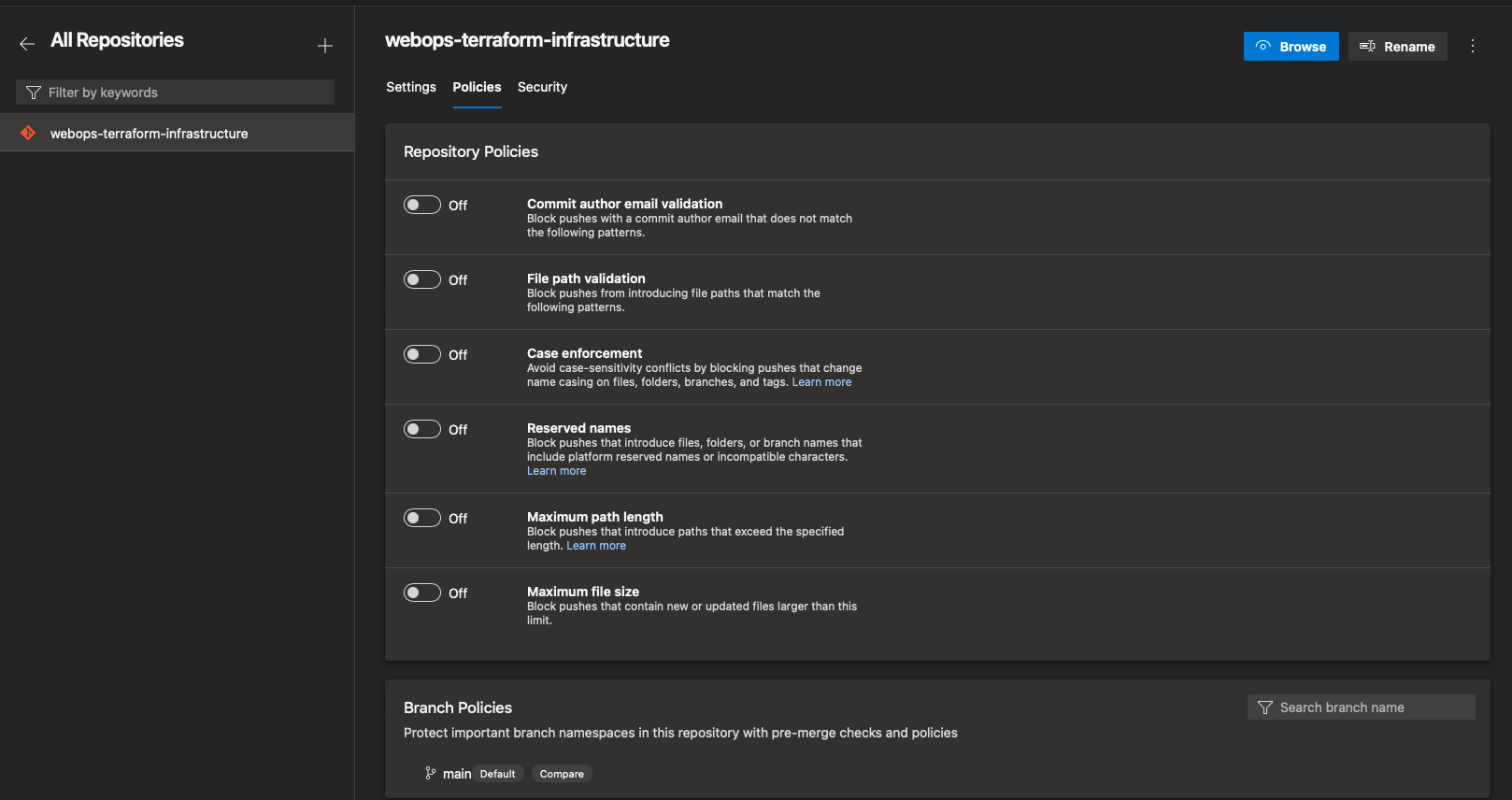
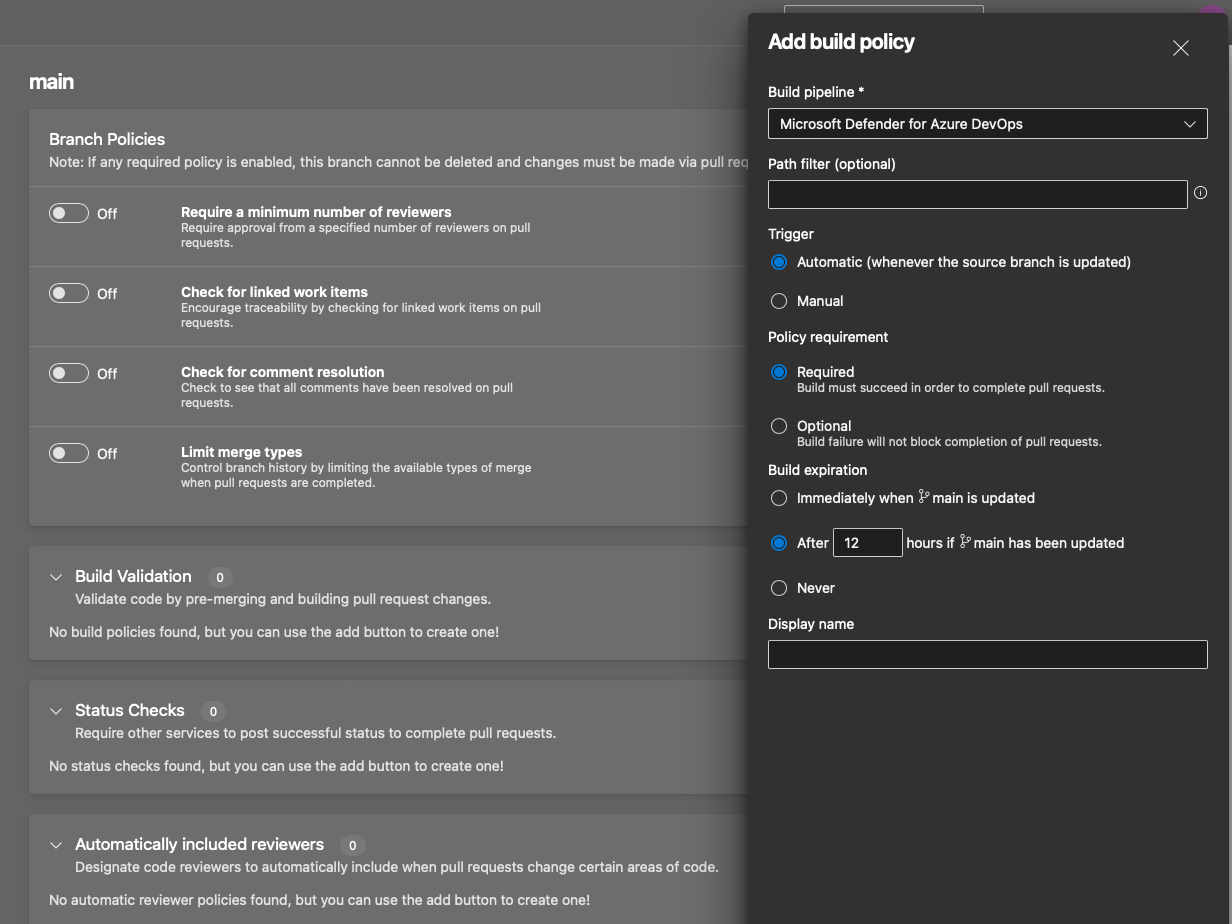
- Select build validation and click the + symbol to add a new build validation. Select the build pipeline you want to use and give it an appropriate name, then click save.
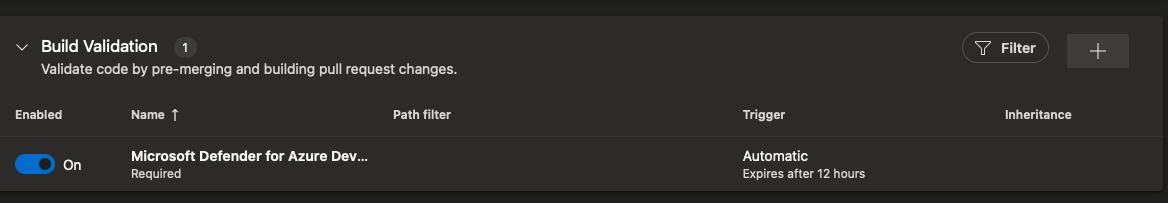
Navigate back to Azure Portal Defender for Cloud and click on DevOps Security. You noticed the repo pull request status is off. You will need to click on configure option and switch it on. This option is the annotation in Pull Requests (PR), so developers can remedy any issues. This process can prevent and fix potential security vulnerabilities and misconfigurations before they enter production.
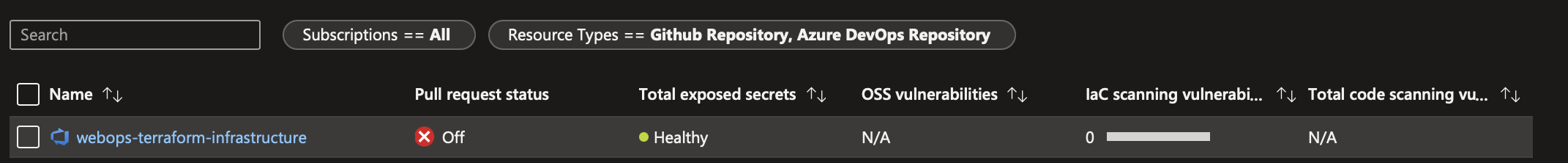
You noticed the repo pull request status is off.

When you click on the Repository name, you will see the results of the pipeline run with any recommendations and alerts found. As you can see, one Severity high alert suggested that “Code repositories should have secret scanning findings resolved.”

I hope you learn something and see how easy it is to set up Microsoft DevOps Security in Defender for Cloud for Azure DevOps. There are also other features, like using workbooks to monitor the security of your Azure DevOps environment. Next, I will show you how to set up Microsoft DevOps Security in Defender for Cloud for GitHub.
References
- https://learn.microsoft.com/en-us/azure/defender-for-cloud/azure-devops-extension
- https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-devops-introduction
- https://marketplace.visualstudio.com/items?itemName=sariftools.scans
- https://www.microsoft.com/en-us/security/business/cloud-security/microsoft-defender-devops

